Your AI Agent Needs an ID Card, Not Just a Password
The "Agentic World" is here.
We aren’t just using AI to summarize emails anymore. We are building systems where autonomous agents act on our behalf—accessing databases, deploying code, and moving money. It is a massive leap forward in productivity, but it introduces a terrifying new security reality.
If an autonomous agent has the keys to your kingdom, what happens when it gets hijacked?
Traditional security models were built for humans who act slowly and predictable. They crumble when faced with machine-speed attacks. To secure this new frontier, we need to stop relying on static secrets and start treating AI agents with the same rigorous scrutiny we apply to strangers.
We need Zero Trust.
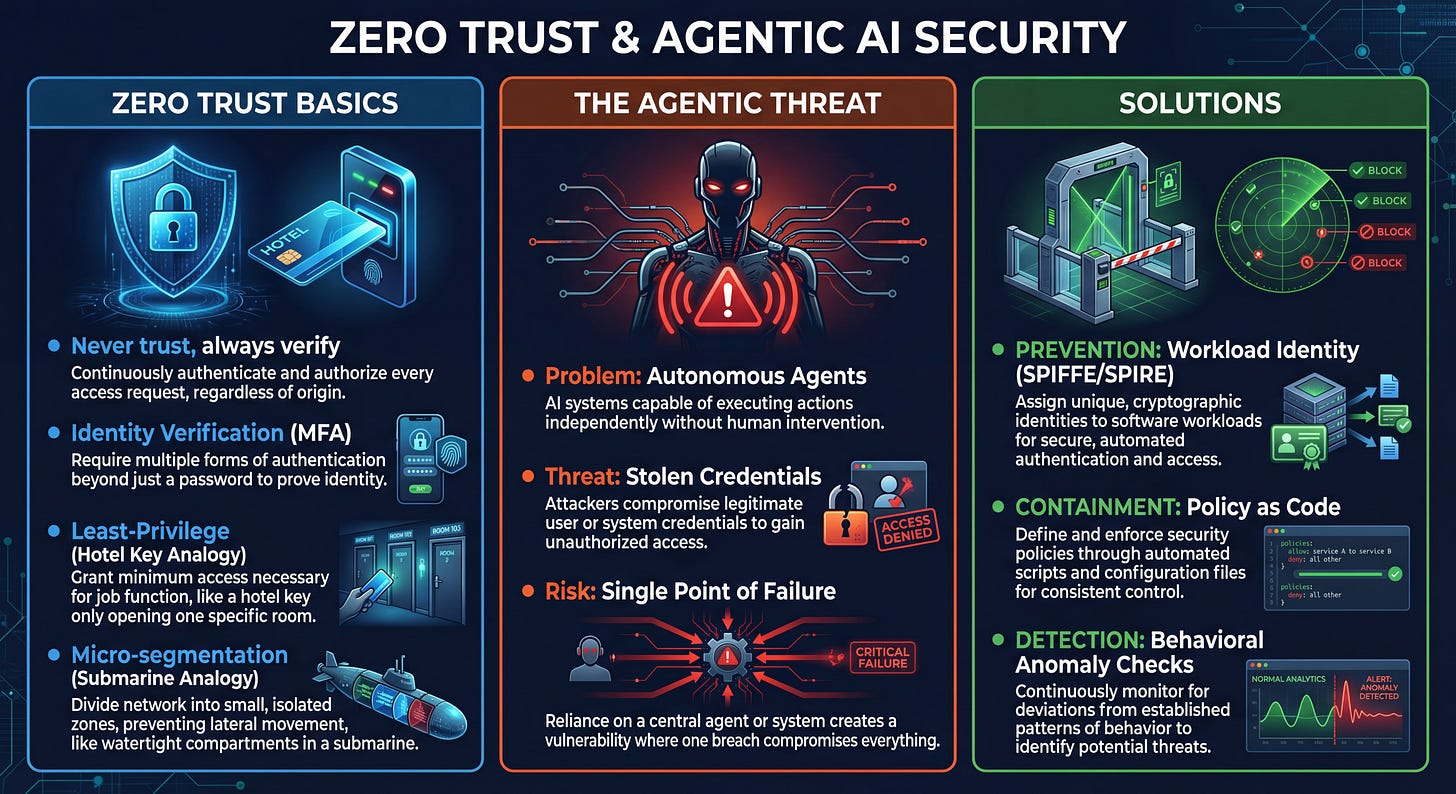
The Basics: Never Trust, Always Verify
Before we dive into the robot uprising, let’s ground ourselves in the core concept.
Zero Trust is exactly what it sounds like. It discards the old “castle-and-moat” idea—where everything inside the firewall was trusted. In a Zero Trust world, we assume the network is already compromised. No user, no device, and certainly no AI agent is trusted by default.
Every single request must be verified. Not just once at login, but continuously.
The Threat: The “Bearer Token” Problem
Here is the twist with Agentic AI.
Humans have multi-factor authentication (MFA). You have a password and a phone. If a hacker steals your password, they are still stuck.
AI Agents, however, usually rely on API Keys or Bearer Tokens. In the security world, a bearer token is like cash. If you drop a $100 bill on the ground and someone picks it up, they can spend it. The cashier doesn’t check if the bill belongs to them; they just check if the bill is real.
If an attacker steals your agent’s API key, they become the agent. They inherit all its permissions, all its access, and all its power. Because agents are designed to be autonomous, the attacker can execute thousands of malicious actions before you even wake up to check your logs.
The Solution: A New Architecture
We cannot fix this by just “hiding the keys better.” We need a fundamental architectural shift based on three pillars: Prevention, Containment, and Detection.
1. PREVENTION: Strong Workload Identity (The “ID Card”)
We need to stop asking agents, “What key do you have?” and start asking, “Who are you?”
This is where Workload Identity comes in. Instead of giving an agent a long-lived secret key (which can be stolen), we give it a cryptographic identity based on what it is.
Using frameworks like SPIFFE/SPIRE, an agent must prove its identity to the system by:
verifying its code hash
the server it’s running on
and the user it’s serving.
Only then does it get a short-lived “ID Card” (like an SVID).
This ID expires every few minutes. Even if an attacker manages to steal it, it becomes useless almost immediately.
2. CONTAINMENT: Policy as Code (The “Real-Time Check”)
Giving an agent an ID card is step one. Step two is making sure it doesn’t abuse its power.
In the old model, if you had a key, you could open the door. In the Zero Trust model, we use Policy as Code to check every single attempt to open a door.
We don’t just grant blanket access. We enforce Proactive Authentication and dynamic permissions. A policy engine sits in the middle of the conversation and asks context-aware questions for every request:
“I know you are the ‘Invoice Agent’, but why are you trying to read the ‘Payroll Database’?”
“Why are you trying to delete 10,000 records at 3:00 AM?”
If the action violates the policy, the system blocks it instantly—stopping long-running malicious activities dead in their tracks.
3. DETECTION: Behavioral Anomaly Checks (The “Safety Net”)
Finally, we must “Assume Breach.” We assume that despite our best efforts, a clever attacker might still find a way in.
This is where Observation becomes critical. We monitor the behavior of our agents. We establish a baseline of what “normal” looks like.
Does this agent usually send 5MB of data?
Does it usually talk to this specific IP address?
If a trusted, verified agent suddenly starts acting strangely, like exporting massive amounts of data or probing new network ports, we treat that anomaly as a threat immediately.
The Bottom Line
Security in the agentic world isn’t about building higher walls; it’s about better guards.
We are handing over immense power to autonomous software. To do that safely, we must move away from static credentials and embrace a world where identity is proven, access is dynamic, and behavior is constantly watched.
Your AI agent is a powerful employee. Make sure you verify its ID.

Great article 👏🏻